On 12 May 2017, WannaCrypt made the news about ransomware, this is the date when WannaCry ransomware began affecting computers worldwide. The initial infection might have been either through vulnerability in the network defenses or a very well-crafted spear phishing attack.
The WannaCry incident is both new and scary. The ransomware uses a vulnerability first revealed to the public as part of a leaked stash of NSA-related documents in order to infect Windows PCs and encrypt their contents, before demanding payments of hundreds of dollars for the key to decrypt files.
This attack had managed to infect large
numbers of computers across the health service less than six hours after it was
first noticed by security researchers, in part due to its ability to spread
within networks from PC to PC.
Here's what I know and what the masses out
there need to understand about this and indeed about ransomware in general. But
before that here are some basics about ransomware.
What
is ransomware?
Ransomware is a particularly nasty type of
malware that blocks access to a computer or its data and demands money to
release it.
How
does it work?
When a computer is infected, the ransomware
typically contacts a central server for the information it needs to activate,
and then begins encrypting files on the infected computer with that
information. Once all the files are encrypted, it posts a message asking for
payment to decrypt the files – and threatens to destroy the information if it
doesn’t get paid, often with a timer attached to ramp up the pressure.
How
does it spread?
Most ransomware is spread hidden within
Word documents, PDFs and other files normally sent via email, or through a
secondary infection on computers already affected by viruses that offer a back
door for further attacks.
Now let’s come back to WannaCry
What
is WannaCry?
This malware is a scary type of trojan
virus called “ransomware.” As the name suggests, the virus in effect holds the
infected computer hostage and demands that the victim pay a ransom in order to
regain access to the files on his or her computer.
RansomWare like WannaCry works by
encrypting most or even all of the files on a user’s computer. Then, the
software demands that a ransom be paid in order to have the files decrypted. In
the case of WannaCry specifically, the software demands that the victim pays a
ransom of $300 in bitcoins at the time of infection. If the user doesn’t pay
the ransom without three days, the amount doubles to $600. After seven days
without payment, WannaCry will delete all of the encrypted files and all data
will be lost.
How
much are they asking for?
WannaCry is asking for $300 worth of the
cryptocurrency Bitcoin to unlock the contents of the computers.
Will
paying the ransom really unlock the files?
Sometimes paying the ransom will work, but
sometimes it won’t. For the Cryptolocker ransomware that hit a few years ago,
some users reported that they really did get their data back after paying the
ransom, which was typically around £300. But there’s no guarantee paying will
work, because cybercriminals aren’t exactly the most trustworthy group of
people.
There are also a collection of viruses that
go out of their way to look like ransomware such as Cryptolocker, but which
won’t hand back the data if victims pay. Plus, there’s the ethical issue:
paying the ransom funds more crime.
How
was WannaCry created?
The creators of this piece of ransomware
are still unknown, but WannaCry is their second attempt at cyber-extortion. An
earlier version, named WeCry, was discovered back in February this year: it
asked users for 0.1 bitcoin (currently worth $177, but with a fluctuating
value) to unlock files and programs.
How
can I protect myself from WannaCry?
CVE-2017-0143 (patched in MS17-010), 2017-0016 (patched in MS17-012), or a similar SMB vulnerability. We recommend applying the associated Microsoft patches, disabling SMB v1, and blocking all versions of SMB at the network boundary by blocking TCP port 445 with related protocols on UDP ports 137-138 and TCP port 139 for all boundary devices. Also you can find customer-guidance-for-wannacrypt-attacks here.
OR
OR
Deep
Dive into WannaCry :-
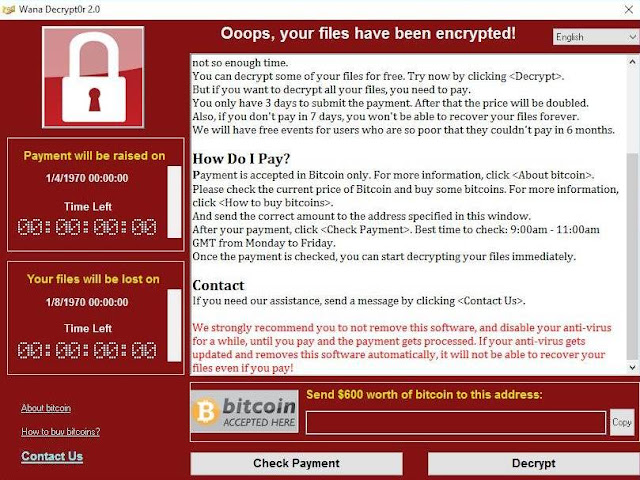
The ransomware WannaCry 2.0 uses the .WNCRY file extension and is reported to be a new version of the WannaCry, also known as WCry family of ransomware viruses. According to reports, this ransomware was used to encrypt the machine files of the initial victim and then leverage a remote command execution vulnerability through SMB, to distribute the ransomware to other Windows machines on the same network. Files are encrypted with the .WNCRY file extension added to them. In addition to this a ransom note is added, named @Please_Read_Me@.txt. Also adds a lockscreen, named “WanaCrypt0r 2.0”.
The ransomware WannaCry 2.0 uses the .WNCRY file extension and is reported to be a new version of the WannaCry, also known as WCry family of ransomware viruses. According to reports, this ransomware was used to encrypt the machine files of the initial victim and then leverage a remote command execution vulnerability through SMB, to distribute the ransomware to other Windows machines on the same network. Files are encrypted with the .WNCRY file extension added to them. In addition to this a ransom note is added, named @Please_Read_Me@.txt. Also adds a lockscreen, named “WanaCrypt0r 2.0”.
The ransom is $300 and you've got 3 days to
pay before it doubles to $600. If you don't pay within a week then the
ransomware threatens to delete the files altogether. Note the social
engineering aspect here too: a sense of urgency is created to prompt people
into action. A sense of hope is granted by virtue of the ability to decrypt a
sample selection of the files. (Note the "Wana Decrypt0r" title on
the window above: the three terms WannaCry, Wcry and WannaCrypt are all
referring to the same piece of malware, they're merely various representations
of the same name.)
The malware spread via SMB, that is the
Server Message Block protocol typically used by Windows machines to communicate
with file systems over a network. An infected machine would then propagate the
infection to other at-risk boxes.
Execution Flow :-
More details about WannaCry ransomware
Execution Flow :-
More details about WannaCry ransomware
CVE
Numbers:
- CVE-2017-0143
- CVE-2017-0144
- CVE-2017-0145
- CVE-2017-0146
- CVE-2017-0147
- CVE-2017-0148
Platform:
Windows
Affected
Version:
NOTE:-
- Microsoft Windows Vista SP2
- Windows Server 2008 R2 SP1 and SP2
- Windows XP
- Windows 7
- Windows 8.1
- Windows RT 8.1
- Windows Server 2012 R2 and
- Windows 10
- Windows Server 2016
NOTE:-
- As usual Mac remains unaffected by this Ransomware
Is this the NSA's fault?
This is where it gets a bit political: the
SMB vulnerability Microsoft patched was known by the NSA. We know this because
the Shadow Brokers leak last month referred to it specifically as
"ETERNALBLUE", an SMBv2 exploit.
And sure enough, the vulnerability was
quickly exploited which is not at all surprising given the way in which it had
now been publicly disclosed.
MITIGATION
AND PREVENTION
Organizations looking to mitigate the risk
of becoming compromised should follow the following recommendations:
- Ensure all Windows-based systems are fully patched. At a very minimum, ensure Microsoft bulletin MS17-010 has been applied.
- In accordance with known best practices, any organization who has SMB publically accessible via the internet (ports 139, 445) should immediately block inbound traffic.
Additionally, organizations should strongly
consider blocking connections to TOR nodes and TOR traffic on network. Known
TOR exit nodes are listed within the Security Intelligence feed of ASA
Firepower devices. Enabling this to be blacklisted will prevent outbound
communications to TOR networks.
In addition to the mitigation's listed
above, Talos strongly encourages organizations take the following
industry-standard recommended best practices to prevent attacks and campaigns
like this and similar ones.
- Ensure your organization is running an actively supported operating system that receives security updates.
- Have effective patch management that deploys security updates to endpoints and other critical parts of your infrastructure in a timely manner.
- Run anti-malware software on your system and ensure you regularly receive malware signature updates.
- Implement a disaster recovery plan that includes backing up and restoring data from devices that are kept offline. Adversaries frequently target backup mechanisms to limit the possibilities a user may be able to restore their files without paying the ransom.
References



EmoticonEmoticon