Hi All, In my previous arctice i have described SQL Injection Exploitation using SQLmap
In this article we will see what are the different ways by which we can execute sqlmap tool.
For more information about different commands of sqlmap click here
Process 1:-
For demonstration purpose i will be using bWAPP on my localhost, i will use the same setup which i have shown you in my previous article
URL:- http://localhost/bWAPP/sqli_1.php?title=%27&action=search
Vulnerable parameter : title
So lets start how we can execute sqlmap by capturing the entire request.
Step 1: Capture the request in proxy like burp as shown below
Step 2 : Copy the request and save it in the folder where you have installed your sqlmap
Fig 3: Copying the request which contains vulnerable parameter
Step 3: Copy + Paste it in the folder where you have installed the sqlmap. In my case i have installed sqlmap on below directory:-
D:\Soft_VAPT\SQLmap_windows\sqlmapproject-sqlmap-1b18035
So i will create one text file and will save the request say sqlmap_text.txt
In this article we will see what are the different ways by which we can execute sqlmap tool.
For more information about different commands of sqlmap click here
Process 1:-
For demonstration purpose i will be using bWAPP on my localhost, i will use the same setup which i have shown you in my previous article
URL:- http://localhost/bWAPP/sqli_1.php?title=%27&action=search
Vulnerable parameter : title
So lets start how we can execute sqlmap by capturing the entire request.
Step 1: Capture the request in proxy like burp as shown below
Fig 2: Capturing the request which contains vulnerable parameter
Step 2 : Copy the request and save it in the folder where you have installed your sqlmap
Fig 3: Copying the request which contains vulnerable parameter
Step 3: Copy + Paste it in the folder where you have installed the sqlmap. In my case i have installed sqlmap on below directory:-
D:\Soft_VAPT\SQLmap_windows\sqlmapproject-sqlmap-1b18035
So i will create one text file and will save the request say sqlmap_text.txt
Fig 4: Creating text file on sqlmap folder
Step 4:- Press Ctrl +Shift + Right Click(mouse) to open command prompt
Fig 5: Opening cmd on sqlmap location
Fig 6: command prompt at sqlmap folder location
Step 5:- Now its time to execute sqlmap. The command will be as below
sqlmap.py -r text_file_name -p vulnerable_parameter --level=3 --risk=3
Where,
Target:-
-r = REQUESTFILE Load HTTP request from a file
Injection:-
-p = TESTPARAMETER Testable parameter(s)
Detection:-
--level = LEVEL Level of tests to perform (1-5, default 1)
--risk=RISK Risk of tests to perform (0-3, default 1)
To know more about the different sqlmap command in command prompt type
sqlmap.py --help
So the final command will be
sqlmap.py -r sqlmap_test.txt -p title --level=3 --risk=3
Fig 7: sqlmap command
Fig 8: sqlmap output showing database name
And like wise you can fetch information like
Database Users
Tables in Database
Colums from the user table
Database dump
Process 2:-
What if you are testing application which has NTLM authentication, to know more about how to set NTLM authentication click here.
So if you want to set traffic to pass from your localhost set the command as follow
sqlmap.py --proxy=http://127.0.0.1:8080 -r text_file_name -p vulnerable_parameter --level=3 --risk=3
Where,
Request:-
--proxy=PROXY Use a proxy to connect to the target URL
Now your SQLMap will attack on your web application through Burp suite which is already taking care of NTLM Authentication.
Process 3:-
If you are testing application in client environment where
=> Application is in UAT and hosted on internet then you must have
- Set up upstream proxy in burpsuite
- Your traffic will be passed from Browser ==> Burp Suite ==> UpStreamProxy
Then it might be possible that cipher suit compatibility issue with application/web server so in that case you might not get proper output in your sqlmap GUI also you will not get any response in your burpsuit history as traffic you are routing is through burp proxy.
Below error you will encounter
1- In Burp response you will get error like
OR
2- In sqlmap you will receive error like below
or
So in that case follow below step to solve this issue :-
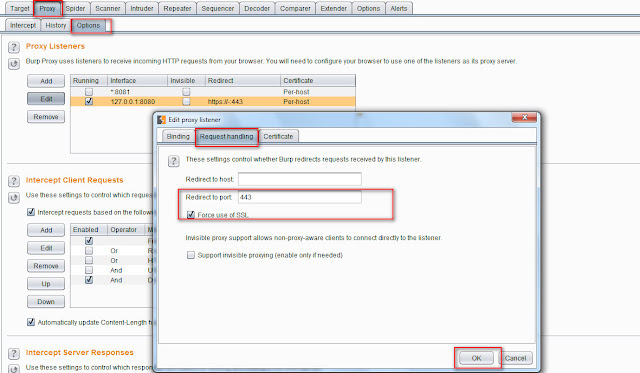
1 - Set up burp suite as follow
By doing above setting at burp level now your sqlmap can easily handle each request.
PS: Make sure in your .txt file you have entered http request
Process 3:-
If you are testing application in client environment where
=> Application is in UAT and hosted on internet then you must have
- Set up upstream proxy in burpsuite
- Your traffic will be passed from Browser ==> Burp Suite ==> UpStreamProxy
Then it might be possible that cipher suit compatibility issue with application/web server so in that case you might not get proper output in your sqlmap GUI also you will not get any response in your burpsuit history as traffic you are routing is through burp proxy.
Below error you will encounter
1- In Burp response you will get error like
OR
2- In sqlmap you will receive error like below
or
So in that case follow below step to solve this issue :-
1 - Set up burp suite as follow
By doing above setting at burp level now your sqlmap can easily handle each request.
PS: Make sure in your .txt file you have entered http request
Soon i will be updating many other techniques of using sqlmap. Stay tuned :)
Thanks you.












EmoticonEmoticon