Recently while participating into AT&T Bug bounty program i have submitted bunch of bugs. Yes bunch of bugs. Well as i have already blog posted many bugs like XSS, CSRF etc. So rather then blog posting those bug i will be describing one interesting bug which is Host header injection.
Introduction:-
What is Host Header Injection ?
As the name suggest host header injection is attack in which an attacker can manipulate the Host header and cause the application to behave in unexpected ways. Header simply specifies which web site should process the HTTP request. The web server uses the value of this header to dispatch the request to the specified website. In short if any malicious user is able to handle this header to their desired domain and if server is not validating it then it leads to host header injection
Why this happens ?
HTTP header injection occurs when Hypertext Transfer Protocol (HTTP) headers are dynamically generated based on user input.
OR
ANY site that does not validate HTTP Host: headers.
How to find this bug ?
Verify the header of the request. Inject other domain in the header field and check the response.
What is impact of this bug ?
An attacker can simply send the wrong host in the requests and poison the cache of proxies/web server. It has nothing to do with the browser's cache.
Next time, a legitimate user tries to access the correct host but since the cache of the web server is poisoned with the attacker's domain, the legitimate user will be redirected to the attacker's domain.
Do NOT use the value of the Host header for anything.
Proof Of Concept:-
So basically I was able to control the host header of AT&T. Below is the POC Request and Response.
POC Request-
GET /shopping-cart HTTP/1.1
Host: telephones.att.com
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Modified POC Request-
GET / HTTP/1.1
Host: google.com
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
POC Payload -
Host: google.com
Host: anymalicioussite.com
POC Response
HTTP/1.1 301 Moved Permanently
Date:Fri,03 Jul 2015 08:52:16 GMT
Location: http://google.com
Content-Length:226
Keep-Alive:timeout=5,max=100
Connection: Keep-Alive
Content-Type: text/html; charset=iso-8859-1
After reporting this bug they fix this issue as below:-
HTTP/1.1 400 Bad Request
Date: Sun, 18 Oct 2015 14:22:41 GMT
Server: Apache
Content-Length: 226
Connection: close
Content-Type: text/html; charset=iso-8859-1
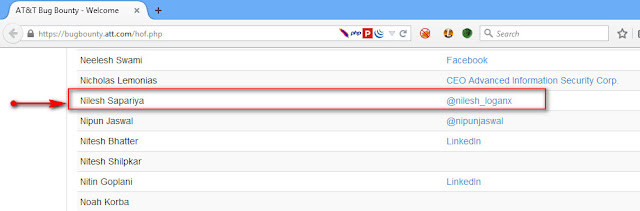
AT&T fixed this issue and put my name on their security acknowledgements list.
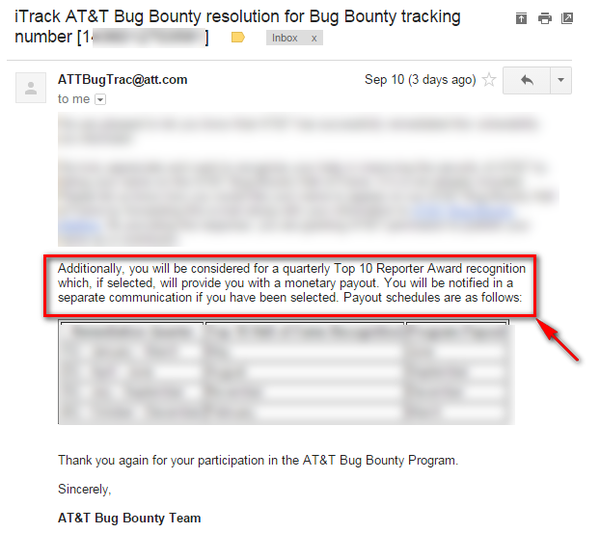
As I mentioned earlier I have reported bunch of bugs and Host header injection is one of them so after fixing my all submitted bugs, they selected me for quarterly Top 10 Reporter Award :)
So wish me Luck :)
Video POC:-
Below is the video POC demonstration of this attack
Time-Line:
Vulnerability timeline:
July 04, 2015 at 11:25 AM : Reported to AT&T Team
July 20, 2015 at 10:15 PM : Received initial reply from AT&T Team
Aug 06, 2015 at 11:19 PM : AT&T Team released a quick fix for the vulnerability
Oct 25, 2015 at 09:30 PM : Public responsible disclosure

6 comments
Write commentsAmazing bro!!!!
ReplyThank you.
Replygreat finding bro :) good luck for top 10 (i am also in race :P 3 bug verified ..3 more to go)
ReplyThank you. Never be in race, but yes race with yourself ;) #JustSaying
ReplyHey naresh, so it is a HOST header inejction, means you inject the host header to any other domain and then it redirects to that domain, so it is a vulnerability?
ReplyHi, First of all my name is Nilesh :)
ReplyWell if your browser cache the header then YES it is.
EmoticonEmoticon